Horizontall
Writeup
Difficulty : Easy

Port Scan
2 ports were open in this machine : 22, 80
Subdomain
There were no intresting directories for the website so I moved to find the subdomain
One of the js files had the subdomain which saved a lot of time in scanning
Js file link :
http://horizontall.htb/js/app.c68eb462.js
Subdomain found :
api-prod.horizontall.htb( Add the subdomain in/etc/hosts)
Directories
web Exploitation
Alright, so among all the directories , the /admin was userful
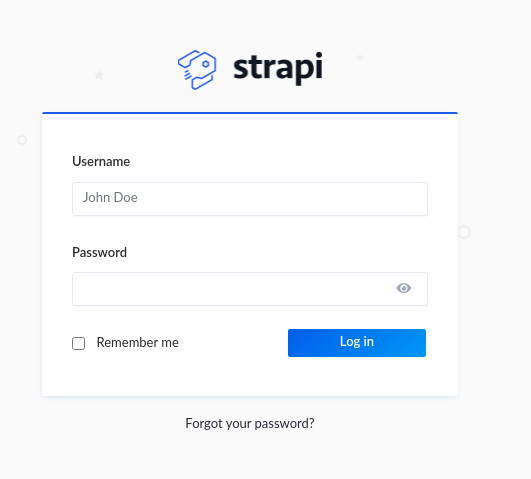
It uses starpi cms
What's Starpi ?
Strapi is an open-source headless CMS used for building fast and easily manageable APIs written in JavaScript. It enables developers to make flexible API structures easily using a beautiful user interface. Strapi can be used with various databases including MongoDB, PostgreSQL, etc.
Starpi Version
I didn't found anything on the website that tells us the starpi version
So, I used feroxbuster again, to find sub directoires.
I found an intresting directory that gaves the starpi version used in the server (
http://api-prod.horizontall.htb/admin/init)
starpi verison is :
3.0.0-beta.17.4
Exploit
Public exploit link :
https://www.exploit-db.com/exploits/50239Download or copy the exploit to get login details
Login details :
Login details : [ admin:SuperStrongPassword1 ]
User Shell
Exploit link for RCE :
https://github.com/diego-tella/CVE-2019-19609-EXPLOIT
We got the user shell
User flag
Enumeration
There were some ports open listening on localhost
Enumerate port 8000
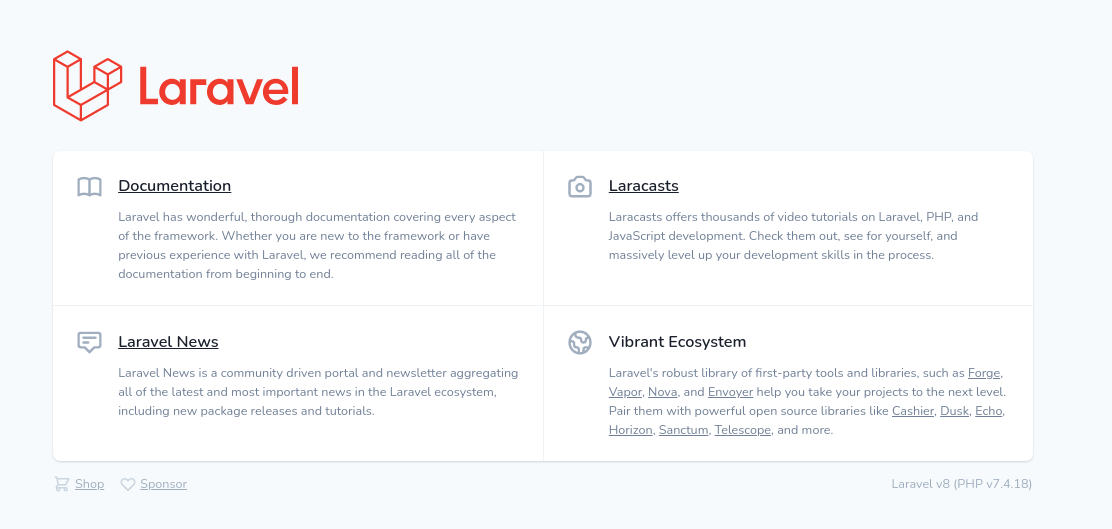
Vulnerable application :
Laravel v8 (PHP v7.4.18)
SSH port forwading
We have the permission to write in
/opt/strapi
We will add our .pub file in the machine to get a shell and for port forward
Required Files for port forward
SSH keys
use
ssh-keygen -t rsato create 2 filesid_rsaandauthorized keysLearn more about port forwarding :
https://phoenixnap.com/kb/ssh-port-forwardingRename the
.pubfile toauthorized_keysand the other file toid_rsaDownload the
authorized_keysin the machine in/opt/strapi/.sshI've used python3 server
wget it in the machine
Root Shell
Homepage of the application running on port 8000
Exploit used to get root priviliges :
https://github.com/nth347/CVE-2021-3129_exploit
Root Flag
Root Shell (nc part)
Open nc connection on any port
shell
Last updated